Key Data Security Tips for Businesses and Organizations
The world has experienced an incredible growth in technology over the past couple of decades. Inception of the internet was probably the greatest invention in the world of technology. It connects people from all corners of the world easily and has become the center of operations in every industry, especially with issues of data and communication. The more the internet gets used, the more data privacy and security questions arise. Internet data security is a big topic of public interest, especially after the US Senate grilled Mark Zuckerberg on allegations of data privacy breach by his company – Facebook, back in 2018. More recently, TikTok CEO Chew appeared before US congress to answer questions as scrutiny mounts on the app's relations to China, where ByteDance, the parent company of TikTok operates from.
Data security and privacy concerns have a huge bearing on the corporate world as well as the private space of individuals. There are risks and a threat posed by internet security breaches, especially in relation to a company's sensitive data. Therefore, an organization should come up with mitigation measures that ensure their data is safe and secure from access by unauthorized persons.
Breach of data security has become commonplace through internet maneuvers, putting sensitive organizational information on a trail of risks and threats. It is, therefore, fundamental to understand issues related to data security; hence in this article, we investigate the risks and threats posed by internet data security concerns to organization's information. Further, we explore the consequent challenges of illegal access to this data as well as possible measures to reduce the risk of losing data or having it accessed by unauthorized persons.
The first stage of dealing with a challenge is; understand the cause of the challenge.
To help shape the conversation, we will pose the following questions:
- To help shape the conversation, we will pose the following questions:What risks and threats to data security emanate from the internet?
- What challenges do they pose to the organization?
- What policies and procedures can the organization use to mitigate and reduce the risks and threats?
The answers to these questions will help in number of ways. First, managers of organizations that use the internet frequently for their operations shall understand the risk posed by the same to the data they upload and share online. After understanding this, it shall help them formulate policies and procedures to ensure that their data remains secure and away from illegal access.
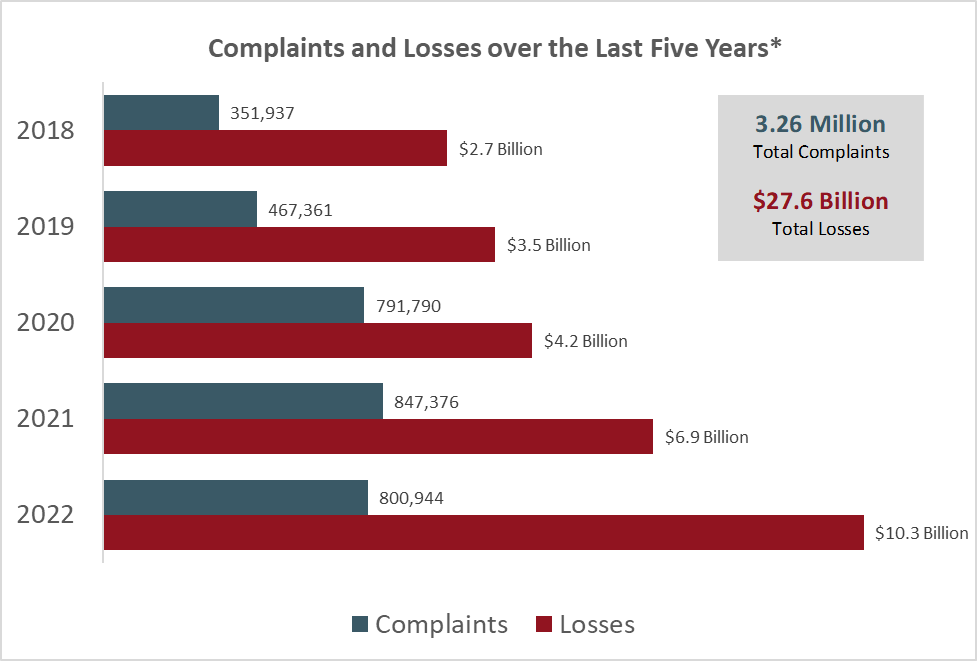
Firms have been losing billions of dollars whenever their data is illegally accessed by unauthorized persons. According to a 2022 report by Internet Crime Complaint Center (IC3) the total losses as a result of cybercrime-related issues was $10.3 billion, up from $6.9 billion in 2021. In fact, IC3 demonstrates that this number has been increasing for the last 5 years, since 2018.
As a result, firms need to keep strengthening their data security measures every passing day, technology is revolutionary, and managers and top executives must be up to scratch with the latest developments if they are to protect their firm's critical information. The role of management should be seeking to seal the vulnerabilities that internet security concerns bring to their organization. Data encryption, authentication processes, malware detection software, and virus protection are all procedures possible for data protection, but an organization must establish how they specifically fit into their case.
Common Threats and Risks to Data Security in Business
There are different risks and threats that challenge the very security of company data. The following risks and threats shall be discussed in detail;
a) Disgruntled and rogue employees: The most important part of any organization is the employees. They drive the agenda of the firm ahead, and thus must be trusted with the organization's system. However, conflicts arise within a firm, and employees become disgruntled. This sense of dissatisfaction makes them a weapon against their own employers, and enemies can easily trike from that perspective. They can easily give access to classified information to authorized persons as a way of vengeance against an organization that has made them angry.
b) Carelessness by the workforce: Employees not only get hurt and angered by the organization, rather they can become careless at times. This comes in the form of leaving systems logged in and the workplace exposed. Any person who gets to their work station can easily access data from the systems, risking the privacy of the same.
c) BYOD: It is a common strategy known as Bring Your Own Device. Organizations sometimes find it prudent to allow employees use their own devices like personal computers and tablets for work related purposes. This is a risky move to allow personal gadget access the systems because the organization shall already have entrusted its data to a third party other than itself. Employees' personal gadgets can be accessed by a whole lot of people, making it difficult to control organizational data privacy.
d) Third party service providers: It is common practice for firms and businesses to outsource for services from outside the firm itself. Technology services are usually outsourced especially networking and cloud hosting. This can be manipulated by tech gurus, leading to illegal access of information and subsequent breach of privacy.
e) Unpatched devices within the organization's network: There are devices that have no updates whenever vulnerabilities are discovered. In most cases, vulnerabilities are patched using software updates. These unpatched devices which expose the firm to the probability of losing data, or having it attacked by cyber criminals in course of operations.
Some of the threats are internal and can be controlled or eliminated using internal mechanisms, while others are external and need policies and procedures to help the business adapt to the threats.
Impact of Illegal Data Access to Businesses and individuals
The reason why they are risks and threats is because they bring rise to challenges within the business. Some of the challenges that result from the challenges striking include;
1. Loss of important company data. Organizations have very important information that they store in their systems. Most crucial is their customer data and financial data. Illegal access to this information brings up the risk of losing that kind of important information, which would be a massive setback for any firm. Loss of such data may affect decision making as the fact checks may be unavailable.
2. Illegal access of sensitive company information. Even without losing data, illegal access to sensitive company information may be detrimental competitors and opponents may use this kind of information to defame and fight against the firm. For any firm that is profit-oriented, having their information accessed to, is huge challenge.
3. Leaking of classified information that should only be accessed by authorized persons. This usually happens to institutions like government agencies and such. For instance, the US government is highly secretive on security matters. In 2016, former First Lady and Secretary of State – Hillary Clinton – faced a huge uproar because Russian hackers had accessed her private data related to matters of national security illegally. Such breach of data privacy has the ability to cause national concern on security of citizens.
Policies and Procedures to Reduce the Risks
A company should ensure that their information always remains secure and safe, and that can be ensured through development of policies and procedures regarding mitigation of risks. Some of the ways that this can be done include;
a) Termination of dormant accounts: This is a good policy that helps improve accountability. When using the systems, every activity should be traced to a specific working account. Therefore, if an employee does not use their account for a certain period (say a month), it should be deactivated. This should help improve credibility and avoid suspicious activity that cannot be traced to any single person.
b) Organized training workshops focusing on data security: Employees need to be trained on the importance of data security. It may not be an overnight act making them understand the intrigues of data security and privacy. Therefore, monthly workshops aimed at training them, on the latest issues related to data security should help secure the organization's systems.
c) Monitoring of activity in privileged accounts: Privileged accounts carry massive weight on the operation of the organization. As such, they are usually the ones prone to external attacks. Further, they are the ones that pose the greatest risk if illegally accessed. Therefore, it is important for management of any organization to set up a system that monitors activity in such accounts. Any suspicious acts should be countered to avoid any data privacy breach.
d) Fingerprint biometrics to login into company systems: Security must begin with internal mechanisms. Biometric logins ensure that nobody can login into an account if their fingerprints cannot be recognized by the system. By adopting this mechanism, the organization shall make it hard for any unauthorized person to crack the access to data, thus ensuring more security.
e) Complete ban on the BYOD strategies: At times this strategy improves the productivity of employees as employees enjoy working with their own devices, but at other times it's detrimental to organizational data security measures. For the sake of data security, businesses should ban use of personal devices for work related functions.
f) Data backup plans: Sometimes, the possibility of losing data to illegal activities is beyond the control of the business. Therefore, the organization should have data back up plans that ensure even if one system is interrupted, they can still have their data intact in another independent system.
The suggestions above on policies and procedures cannot be implemented in the same way for every organization. It is fundamental that they be treated as skeleton provisions that need proper tailoring to fit the individual needs of an organization. Leaders should come together and formulate a plan on which policies to adopt and how to implement them for the better good of the organization. The principle issue of concern should be securing a firm's information, and keeping it tightly in the grip of the business
... In Conclusion
Data security has become a really huge concern with increasing cybercrime. Companies are trying to reorganize their systems to repel the risks and threats that come from internet security concerns. A huge responsibility of ensuring that data protection is a success lies on people who deal with the systems on a daily basis – the employees. If they expose the system to fraudsters, the organization is likely to lose a massive amount of data. Therefore, the organization should set up procedures and policies that are likely fed off the challenges that arise when data security is breached. The future is great for organizations that shall adopt measures of data security, and could be bleak for those that shall not. Every new day comes with new technologies, hence the need to remain updated on the happenings around the technology world. This should help an organization put in place measures that wrap its data against the possibilities of illegal access.