What is Typosquatting? Examples of Typosquatting
Definition of typosquatting. Types of domain typosquatting and examples. Purpose of typosquatting attacks and how to protect yourself and your online business from typosquatting attacks
We have all been in situations where a word in a printed or typed text has a spelling mistake. If a single letter in a word is changed, added, or entirely removed, the mistake is commonly known as a typo. From these experiences, we have come to learn that typos can change an entire word's meaning in a humorous way or embarrassing, depending on your contribution to the typo. One of the meanings of squatting, on the other hand, is to illegally occupy a space such as a building or a piece of land. These are grammatical definitions and you might ask yourself, what do the words have to do with cybersecurity? Well, it is all about their combined word, typosquatting.
Typosquatting in Cybersecurity
You might have heard the explanation but not put a name to it. Typosquatting is a common name when it comes to cybersecurity, more so internet security. All the big organizations have become victims of typosquatting, including Google, Yahoo, Apple Inc, PayPal, Amazon, Netflix, and even the all-new TikTok.
Here are some of the questions we will be addressing in this article:
1. What is typosquatting?
2. What are examples of typosquatting?
3. How is typosquatting used?
4. Any typosquatting protection tips?
What is Typosquatting? Typosquatting Definition
Whereas typos are unintentional, typosquatting is not. Typosquatting involves the registration or purchase of a domain that closely resembles a legitimate website's name or domain. Since these mistakes are intentional, people who own or operate these domains often have a malicious attempt and hence are cyber-attackers - or simply attackers.
Example of a Typosquatting Attack
As normal and frequent users of major websites, we know the websites' URLs by heart. For Google, we know it's , for Facebook, it's , Amazon , and so on. So instead of searching the name, Google, Facebook, and Amazon on a browser's search box and clicking on a relevant web result that corresponds to the brand, we sought to enter the URL in a browser's URL box and bypass the whole search process. We have a good reason to do that, after all, we consider those seconds very precious.
But wait, here is the problem.
Browsers do not correct spelling mistakes in URLs since there isn't a rule on the grammatical correctness of a domain or URL. If you write any name in the URL box that has a .com for instance two things will happen. Either the web page will be returned if it exists or you get the page below:
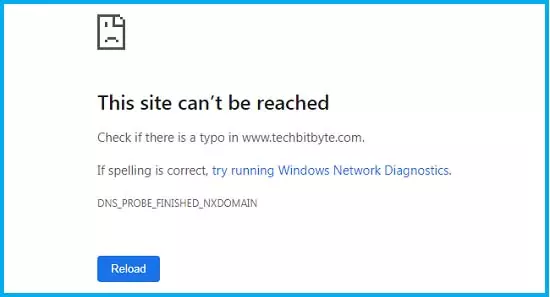
Did you notice the typo in the URL? We searched for www.techbitbyte.com other than the correct www.techbitbytes.com.
Attackers know this, and also know of our persistence to directly navigate to websites from the URL box (not through a search engine's web results). So what does an attacker do with this information? An attacker will look at the common typos users make in domain names on the URL box, and register or purchase domain names with those names. For instance, , , , and so on. When you now make a typo when trying to reach and you type , you will be taken to the illegally set up . Once you are in the attacker's domain, literally, you can easily become a victim of the attack since that domain was set up for any number of reasons, which are many from collecting user information to downloading malware to a user's device, conducting an affiliate marketing on products, and so much more.
In our example, if the an attacker had a typosquatting domain , the user would have been directed there other than the intended
Types of Domain Typosquatting
1. Added or Omitted Characters from the Domain Name
This is the most common form of typosquatting. Attackers create a fake website from a legitimate brand and register its domain name as somewhat similar name to the legitimate domain name. The name is often sought from the common typos that users make when directly navigating to a domain from the URL.
For instance, an attacker can omit a letter or character to come up with a fake domain name. Examples include
>
>
>
In another instance, attackers can add letters to domain names and come up with fake domains for illegal websites. Examples include:
>
>
>
2. Hyphenated Domains (Adding Hyphens to Domains)
Some domains are made of two or more words. Take facebook.com for example. Even if it is treated as one name, some people might consider them as two names. With this information, an attacker can register a domain with a hyphen to separate two seemingly correct-looking domain names. Here are examples of illegally hyphenated domains:
Examples include:
>
>
>
>
3. Typosquatting Through Top-Level Domain (TLD) Extensions
Most common domain names end with .com, which is also called a domain extension. Other TLDs can be used for a domain, including .org, .net .co, and many more. Here, an attacker can exploit a TLD typo in the following way:
The attacker can register a domain ( is the legitimate website) and wait for users to be directed to his or her fake website when they make typos in the URL by typing instead of . So, when a user types in the URL box instead of the intended , he or she is directed to the illegal website.
Try search for www.amazon.co, you will be redirect to amazon.com. It is likely Amazon purchased the amazon.co (Colombia) domain to protect their domain from typosquatting.
TLD extensions can also be used for cybersquatting. {Article on Cybersquatting}
4. Omitting the Dot (.) After WWW
A URL structure follows a specific syntax such as , , and so on. However, remember that attackers are capitalizing on common mistakes that users make in the URL box and one common error is to omit the dot after www. An attacker can register a domain with the URL (vs the real ) or (vs the real ). When a user types with the hopes of shopping online on Amazon at , he or she will be directed to the illegal where the attacker will be waiting with malicious intent.
What is the Purpose of Typosquatting?
So you might wonder, why would a person capitalize on the thought that someone would make a typo in a URL? Below, we explore ways in which a user can become a cybersecurity victim by making a simple, and honest, mistake on a domain's URL.
1. Launch a Phishing Scam
Phishing is a cyber threat technique where an attacker impersonates a legitimate person, entity, or organization with the malicious intention of scamming people into believing they are interacting with the legitimate person or organization. Setting up a domain name with the malicious intent of launching a phishing attack. Next, the attacker would have made it look like a legitimate website, and this is where a little IT expertise is needed.
Using free tools such as HTTrack, an attacker can create a copy of the target website where all features including images, fonts, titles, text, and colors match. The only changes the attacker needs are on critical components such as login and signup pages. When users enter their information such as login details (usernames and passwords, addresses, social security information, credit card numbers, and others, in their minds, they are on a legitimate website. After all, it looks exactly the same. However, it is not the same, and soon as users click submit, their data is in the hands of the attacker.
Imagine login into 'Amazon' (A replica of the real Amazon) with the URL (notice the missing 'o'?) and submitting your username and password. Of course, you won't see the real user's dashboard as you often do on Amazon. However, from the simple login, an attacker has enough of your data to launch identity theft, credit card fraud, and even shopping fraud. The attacker will simply get the logins and head to the real Amazon website () and log in using the credentials that you submitted on the fake website. The attacker might change a couple of your details, including your email address such that you won't realize that he or she is shopping on your account. Imagine what an attacker can do with your details such as your SSN, name, and address.
2. Install Malware on Your Devices
Attackers create fake websites and attach malware and other dangerous exploits to them. If you intended to visit but instead searched (notice the missing dot [.] after www?) The fake website might have malware waiting in stealth. Once the page is loaded the malware is auto-downloaded in your device (drive-by download) and can stealthily scan for vulnerabilities to exploit or disguise itself as a critical update (such as a new device driver - think of a popup that requests permission to update your graphics driver) and trick you into installing it.
Once the malware is installed, the attack begins. Depending on the design of the malware and its payload, the attack vector can be ransomware (where your files are encrypted and you are required to pay a certain amount to receive the decryption key) or can be designed to track your activities such as keys (keylogger virus). It can be designed to scan your system for critical data such as ID scans, personal documents, bank statements, personal pictures, certificates, and others and upload them to remote servers managed by attackers. Further, your device can be added to a bot network where it becomes part of a DDOS attack or cryptocurrency mining farm.
3. Sell Goods That Do Not Exist
Some fake websites are designed as e-commerce websites where attackers claim to be selling goods, such as electronics and furniture. Once you pay for the goods, two things will happen:
-
You will definitely lose money. You won't receive the goods that you paid for because they did not exist in the first place.
-
Your personal information such as your credit card, phone number, and address will be compromised, depending on the payment method that you selected during checkout.
4. Run Ads to Monetize Traffic
Attackers can launch typosquatting attacks on high-traffic websites such as Facebook, Google, Youtube, Amazon, and Walmart. The fake websites are then filled with both genuine ads and illegal ads such as drugs and adult-themed products and services. Once users visit these fake websites, they are presented with ads, which the attackers earn revenue from.
5. Run Fake Competitions and Surveys
Fake websites developed from typosquatting can contain content that describes an interesting competition or survey on trending products and services. For instance, a competition-based fake website can claim that if you spin a wheel and land on a winning number, you could win one of the latest gadgets, vacations, or even cash prizes. Of course, the attackers have no such competition and there is a 100% chance you will win. However, you will have to submit your personal details to claim the prize and that's what attackers have been looking for since you landed on their fake website. Other fake websites can run a survey, from which you will be well paid in terms of money or another payment method of your choosing. Just like the competition, the survey is fake and when claiming your payment, your details will be collected and can be used for identity theft, fraud, and other crimes associated with personal details.
Protect Yourself From Typosquatting Attacks
-
Avoid clicking on links on unexpected emails, messages, social media posts, or unfamiliar websites. Fake websites are often buried in these links and you might be a victim of typosquatting attackers by clicking links and visiting sites registered through typosquatting.
-
Avoid opening email attachments contained in unexpected emails or emails that you suspect to be phishing emails.
-
Inspect links before clicking on them or pressing enter in URL boxes.
By carefully inspecting a link, you will be able to spot a missing dot(.) in , an extra 'o' in , and a suspicious hyphen in . -
Save critical websites' URLs in your bookmark tab.
Once you access a legitimate website such as your bank's official website, or shopping site, save it as one of your bookmarks. This will help you navigate directly to the website without manually entering URLs, where you can make a mistake. -
Use search engines' web results to access websites.
Other than directly entering URLs and hitting enter, search for the term in your browser and click on results from the search engine's web results. There is very little chance that a fake website will be shown in the result, and if it does, it will stand out making it easy to spot. -
Use anti-malware and antivirus applications to protect your devices.
Get genuine antivirus and anti-malware products and install them on your devices. Legitimate security products will notify you when software attempts to install. Other internet security products can block websites if they are flagged as fake or have a malicious component. -
Pay attention to browser-flagged websites.
Browsers such as Google and Mozilla display warnings if you try to visit a website suspected to be malicious and dangerous. Pay attention to search warnings and only ignore them if you are absolutely sure that the flag is erroneous.
Protect Your Online Business From Typosquatting Attacks
-
Trademark your domain.
Trademarking a domain ensures that no person or entity can register a domain similar to yours. Further, your domain is protected from being copied without your permission which is not only a trademark violation but also constitutes a violation of federal law in most countries including the US. -
Register typo versions of your domains.
During domain registration, you can also register typo versions of your website. You can then redirect users to the real domain from the typosquatting domain. -
File a Complaint with WIPO against typosquatting domains and websites.
As soon as you discover a typosquatting domain, contact WIPO (World Intellectual Property Organization) and prove that the typosquatting domain is acting in bad faith.
Typosquatting vs Cybersquatting
The are various ways through which domains and domain registrations are abused. In the article above we have discussed one way used to maliciously benefit from domain registrations - typosquatting. Cybersquatting is used to describe all ways that domain registrations are unlawfully done to benefit from the trademark of an individual or company. Therefore, typosquatting is one example of cybersqautting.