Featured Article on TechBitBytes

ARTICLES YOU'LL FIND HELPFUL
How to Create WAMP Virtual Hosts: A Step-by-Step Guide
Learn How to Debug PHP Scripts
6 Common RAM Failure Symptoms: What to Look For and What to Do
How to view computer information in Windows 10 and BIOS
Solved: Aestan Tray Menu Configuration File Error
Examples of Phishing Emails and Their Analysis
Articles That You'll Find Interesting
Cloud Computing Project Risk Management: A Comprehensive Guide
Learn how to use risk management processes to control risks in cloud computing projects. This guide covers the risk management life cycle, risk responses, and documentation.
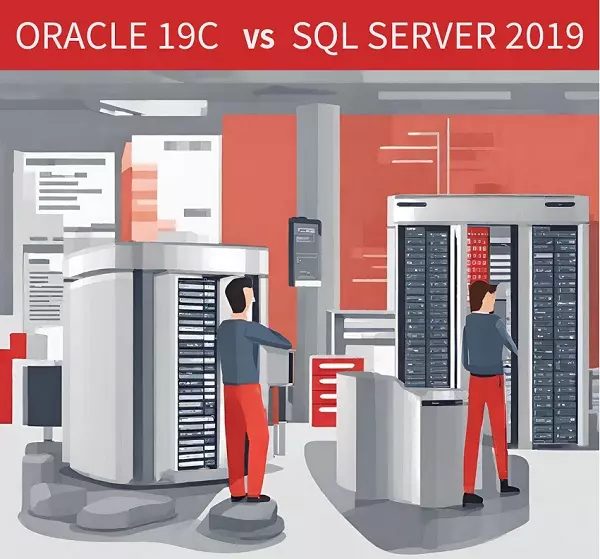
Oracle 19c vs SQL Server 2019: Architecture Comparison
This article compares Oracle 19c Database and SQL Server 2019 Database in terms of memory architecture, physical architectures, and logical architecture. Learn the key differences between these two popular relational database management systems (RDBMS).
Data Security Tips for Businesses and Organizations
Data security is a major concern in the digital age. Learn about the most common threats and risks, as well as the impact of illegal data access and policies and procedures to reduce the risks.
5 Key Data Security Risks in Business and How to Mitigate Them
Learn about the 5 key data security risks and cyber threats that businesses face, and how you can safeguard your business from them. Some common data risks include cyberattacks, disgruntled and rogue employees, and human error.
Cyber Security for Businesses: 5 Solutions to Protect Your Assets
The cloud and IoT have revolutionized the way businesses operate, but they have also introduced new cyber security challenges. This article explores effective 5 critical strategies for overcoming these challenges, with expert insights and proactive measures.
The Impact of Mobile Technology on Society: Benefits and Concerns
Explore the future of mobile technology and how it's transforming healthcare, agriculture, location-based services, and manufacturing. Learn the applications of AI in mobile technology and the use of mobile augmented reality.
BYOD: A Guide to the Benefits, Risks, and Mitigation Strategies
Learn how Bring Your Own Device (BYOD) offers increased productivity, cost savings, and employee satisfaction in the workplace, while managing privacy and security risks with policies and tools.
How to Fix a Freezing Computer: 9 Common Causes and Solutions
Are you experiencing a freezing computer or sudden shutdowns? This article looks into the 9 common reasons why your computer might be freezing or frequently shutting down, and what you can do to fix the problem.
6 Common RAM Failure Symptoms: What to Look For and What to Do
A RAM is one of the most important components in a PC, so it's important to know the signs of a failing RAM. What are the 6 common signs of a failing RAM, and what you can do to troubleshoot the problem?
How to Spot and Avoid Amazon Scams Like a Pro
Amazon scams are on the rise. Read the different types of Amazon scams and learn how you can spot them. Get the ultimate guide on how to avoid amazon scams like a pro.
How to Create Strong Passwords and Securing Your Passwords
Learn how to create strong passwords and how to secure your personal and organizational passwords. Learn the characteristics of strong passwords and using password managers.
Phishing scams: How to Protect Yourself from Phishing Scams
Phishing scams: The Ultimate Guide. What is phishing? Understand the the common types of phishing scams, see examples of phishing scams and learn how to protect yourself from phishing scams.
Exploring White Box Testing in Software Engineering
What is white box testing in software engineering? What are the tools and techniques used in white box testing? White box testing focuses on the internal structure of an application and not just its function.
Black Box Testing in Software Engineering
What is black box testing? Learn about the techniques of black box testing and its types. Read on the advantages, disadvantages, and real-world examples of black box testing.
What is CPU Cache and How Does CPU Cache Work?
What is CPU cache and how does it work? Read on the definition of CPU cache and learn about the L1, L2, and L3 CPU cache types? Read on the differences between L1, L2, and L3 cache.
FREE ONLINE TOOLS THAT MIGHT INTEREST YOU
Lorem ipsum Generator: Generate Dummy Text for Your Designs
Need a dummy text for your graphic and web design templates? Use the online Lorem ipsum generator to tailor your text the number of words, characters, and paragraphs. Customize text in different cases including lower case, upper case, sentence case, random case, and capitalized words.
Strong Password Generator: Online Free Password Creator
Create strong passwords using a free tool online. Generate a strong password and simply copy it into a password input field.
Online Word Counter and Character Counter
Online word counter and character counter. Free online tool to get the number of words and characters in a text. Highlight text to get the number of words and characters.
Free IPv4 & IPv6 Address Generator
Do you need a random and Fake IPv4 or IPv6 address? Our free online generator give you instant access to both IPv4 and IPv6 addresses.
Free MAC Address Generator
Do you need a random MAC address for your network device? Our free online generator give you instant access to fake MAC addresses